Seized UK tanker likely ‘spoofed’ by Iran
GPS spoofing involves ships’ receivers being tricked with counterfeit satellite automatic identification signals generated to gain control of a navigation system. This can take the vessel off course or show it in a different location
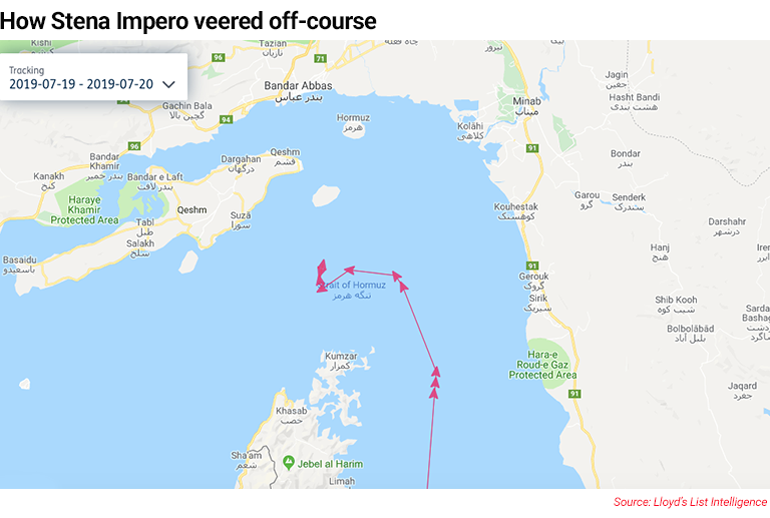
Analysis of AIS data by Lloyd’s List Intelligence shows for the first time that Stena Impero fitted the pattern for a spoofing attack when it was seized by the Islamic Revolutionary Guard Corps on July 19
THE UK-flagged product tanker seized by Iranian forces last month was the victim of technology designed to fool navigation systems.
Evidence appears to show that Stena Impero received “spoofed” Automatic Identification System signals, sending it off course into Iranian waters as it transited the Strait of Hormuz.
Analysis of AIS data by Lloyd’s List Intelligence shows for the first time that Stena Impero fitted the pattern for a spoofing attack when it was seized by the Islamic Revolutionary Guard Corps on July 19.
“Looking at the raw AIS data for the Stena Impero around the time of the incident, there are some strange AIS messages which indicate the GPS used in the AIS message may have been spoofed,” said Lloyd’s List Intelligence analyst Rosie Boyle.
These messages were not processed and thrown out as they were at odds with the speed and trajectory of the vessel, she said.
Furthermore, the timestamp of the messages and the latitude and longitude co-ordinates did not match. These indicators suggest that Stena Impero had been “spoofed”.
So-called GPS spoofing involves ships’ receivers being tricked with counterfeit satellite automatic identification signals generated to gain control of a navigation system. This can take the vessel off course or show it in a different location.
The US Maritime Administration warned on August 8 that vessels could be subject to GPS interference, bridge-to-bridge communications spoofing and communications jamming in the Strait of Hormuz as well as the waters off Oman and in the Middle East Gulf.
The administration cited, but did not name, two vessels that reported GPS interference. It said one vessel shut down its AIS before it was seized, complicating response efforts.
Iran is using GPS jammers to interfere with navigation systems from the island of Abu Musa, an unnamed US defence official told CNN earlier this month.
Iran seized Stena Impero and its 23 crew in a move widely regarded as retaliation for the impounding of the Iranian-controlled very large crude carrier Grace 1 in waters off Gibraltar on July 4.
Iran justified Stena Impero’s capture by saying it had collided with a fishing boat and turned off its AIS to avoid detection by Iran’s navy, violating international maritime rules. While Grace 1 was official released from detention in Gibraltar yesterday, Stena Impero remains at anchor at the port of Bandar Abbas.
The highest-profile maritime spoofing incident was reported in 2017, when 53 ships in the Black Sea were “relocated” during a Russian military exercise.
But spoofing has been linked with North Korean ships, in areas of the Malacca Strait, and most recently in the port of Shanghai earlier this month.
There is no doubt Iran used spoofing technology to interdict Stena Impero, said Roi Mit, marketing officer with Israel-based Regulus Cyber, a cybersecurity company that focuses on spoofing detection and protection.
“This is a classic cyber attack by a state actor,” he said. “If you look at the trajectory of the ship, you see the kind of movement they normally do in the Strait of Hormuz that they have sailed many times. There’s no reason for the ship to suddenly deviate to a completely new location and enter Iranian waters.
“Furthermore, the crew itself reported that day that they were constantly having to repair the route of the ship and that is what usually happens when you’re being slowly spoofed away. The ship is showing it’s straying off course, and you are constantly correcting the course, and that’s when you physically move the ship off course.”
The UK Ministry of Defence said the question of whether or not Stena Impero was spoofed was one for the owners, Stena Bulk.
The MoD has previously said that Stena Impero was captured because it did not provide enough notice to the Royal Navy that it would be passing through the Strait of Hormuz. The British frigate HMS Montrose was accompanying UK-flagged vessels through the passage at the time.
Stena Bulk declined to comment, saying that it was unable to carry out its own investigation into what happened because it had not been able to visit the crew held in Iran.
The company is currently in delicate talks to secure the release of the Indian, Latvian, Russian and Ukrainian nationals working on board the ship.
Some 1,250 vessels monthly transit the Strait of Hormuz, including nearly 600 tankers, data from Lloyd’s List Intelligence shows. That covers some 20m barrels per day of crude and petroleum products.